Computer Networking by Tech4Geek
Certifications show that you know the latest technology. AboutHelpTermsPrivacy. The internet is the largest example of a WAN, connecting billions of computers worldwide. The method returns an array of shape n samples, n classes, where n samples is the number of samples in the test set, and n classes is the number of classes in the problem. These introductory courses include Getting Started with Networking, Getting Started with Cloud, and Getting Started with Wi Fi. Certificate: Yes, with a fee. Copyright © 2021 Makerere University Copyright Complaints DICTS. The current setup allows the DBA to increase this manually. If necessary, they also offer users the technical support and guidance they need among complex wireless or local area network systems. They ensure upgrades and other features don’t cause issues with the website base code. 15 is the working group for WSNs, or wireless specialty networks, such as wireless personal area networks WPANs, Bluetooth, Internet of Things networks, mesh networks, body area networks, wearables, visible light communications, among others. Com are the property of their Hire4Freelance security jobs respective owners. In contrast, a simple home network might need only two devices. What helped me understand it better was being able to see the data being sent over the network. 20 to outbound interface 1. There are many benefits to working in network engineering, especially for women. The world’s 1 eTextbook reader for students. Internet follows standard protocols that facilitate communication between these network devices. You can choose from one of four areas of concentration: computer networking management, digital communications technology, information security, and web technologies. Sign up and learn how you could get your transcripts sent to WGU absolutely free. Higher speeds are available with 10GbE but are not widely available currently and is prohibitively expensive for most equipment. A computer or network crash can lead to business and communication delays, waste of employee time, and loss of precious data or client information. While most remote visualization tools based on the aforementioned methods successfully allow multiple parties to view images from different locations, most also face problems with efficiency and user interactivity at some level. Just like modems, routers are one of the most important parts of any modern network. Similar to a honeypot, a honeynet is a network set up with intentional vulnerabilities. How to Connect to Router Using Console Auxiliary and Protocols.

Peter Odryna
Rudy Faile community member, former podcast guest, navy veteran, and systems engineer joins us to discuss the Handmade movement in 2021, including the Handmade Seattle conference, Handmade projects, and Handmade Network, and where we are planning to go with Handmade Network in 2022 and beyond. I am Java programmer, blogger, working on Java, J2EE, UNIX, FIX Protocol. IGMP Internet Group Management Protocol. You will also receive study guides and practice questions. All organisations and businesses, from government departments to national branches of multinational businesses, need these networks to communicate internally and externally with suppliers, clients and staff. The secret key is never revealed on public domain. Cyber security analysts assess, plan and enact security measures to help protect an organization from security breaches and attacks on its computer networks and systems. DMM in IT related, Science or Engineering subjects. What is the probability that a packet sent by the server is successfully received by the receiver. Subscribe to the blog updates and get deep technical write ups on Cloud Native topics direct into your inbox. Computer networks are used to carry out numerous tasks through the sharing of information. We think one important reason for the success of our book has been that it continues to offer a fresh and timely approach to computer networking instruction. Prepare for the MTA or Azure certification if you wish to learn the principles of computer networking. 2 Speed as close as possible to the speed of current wired networks,. Furniture and supplies are replaceable, and your business will back up and continue running in no time unless you lose the data.
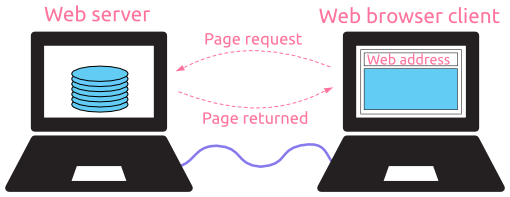
Sycon Zohar
Computer network security consists of measures taken by business or some organizations to monitor and prevent unauthorized access from the outside attackers. This comprehensive resource from Alton Hardin will help you prepare and pass Microsoft’s MTA 98 366 exam on your first try. UK fee payers only see Terms and Conditions for further details. We’re proud to offer IT and security pros like you access to one of the largest IT and security certification forums on the web. This ranges from implementation to connectivity and even security. When it comes to the networking sector, this belief is nothing but a taboo. Network devices, or networking hardware, are physical devices that are required for communication and interaction between hardware on a computer network. Panel A: List of the 7 Compulsory GED courses 21 credit hours. Network Engineering can certainly be self taught. Terms of service • Privacy policy • Editorial independence. Given that propagation delay = 3 sec. By signing up, you agree to our Terms of Use and Privacy Policy. Computers and networks are everywhere. The metrics for this journal are compiled based on the data for scientists listed underElectronics and Electrical Engineering. The purpose is to have a forum in which general doubts about the processes of publication in the journal, experiences and other issues derived from the publication of papers are resolved. Computer hardware maintenance technician. In this program, you will learn Types and Topologies of Computer Networks, IP Addressing, DHCP, NAT, Models, Ports, Protocols, Cables, Wireless Networks and Standards, Mobile Configurations, Network Storage Types, Cloud Based Storage Devices, and much more. Wireless networking is a technology that allows computers and other devices to connect to a network without using cables. Our Master’s in Computer Science specialising in network engineering provides the skills to design and manage computer systems and networks. Judith Kelner, Géza Szabó. As mentioned already, you can use use existing computers or purchase new ones. The diagonal dotted line represents the behavior of a random classifier. Use the left column navigation to refine your search by College, Program Availability, Program Start Date and more, or see the table below for a complete list of computer networking and communications programs at Ontario colleges. We should be able to detect and resolve the issues. Depending on an organization’s requirement or network complexity, the organization will sometimes have global network engineers in different countries who take care of technological advancements throughout the firm. She loves working at Cisco because work and family life balance are prioritized.
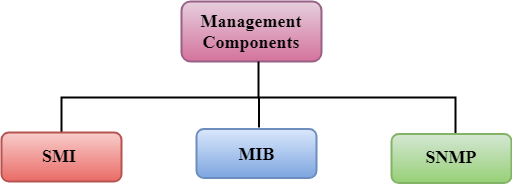
PC Security Advanced
With the help of networking, it is very simple to share all formats of digital data from one computer system to another irrespective of their geographic location. They set up internet connections in many different environments and connect them with physical cables or wireless frequencies, creating adequate signal strength throughout a location for a client’s use. To land any job position, you must prepare for the interview process. Learn about top tech training programs today Get started. Upon completion of the course, you will take a timed, open book exam from your computer. You can build your personalised network of support from the following people and services. There are two main types of wireless networking: 802. Accredited college or university in computer science, engineering, information science, information systems management, mathematics, operations research, statistics, technology management, or a related field. When a domain name in registered with a registrar, it pass on the contact details to the WHOIS. Accelerating energy market analytics through collaboration, networking and alliances. Examples include a master’s in computer and information technology or an MBA with a concentration in info systems or network security. The cabled network cannot communicate with the wireless network and vice versa. Some network architects work for third party service providers who set up and maintain networks for client companies. For network engineering and security. TCP/IP is the globally accepted set of protocols that allow computers and other devices to send and receive data through the Internet. If you are a beginner and want to get good knowledge in networking, then you can learn it from Introduction to Networking course. Will Bob necessarily return the favor and provide chunks to Alice in this same interval. Many degree programs can lead to a career in network engineering. Taught by industry experts. Luckily, there are plenty of scholarships and financial aid available for women in network engineering. 877 729 8266Campus Operator660 543 4111. SolarWinds offers solutions across six areas: network management, system management, security, database management, IT help desk and the cloud. For example, Novel created the Certified Novell Engineer CNE to provide a way to indicate an employee knew and could work on Novell equipment. This compensation does not influence our school rankings, resource guides, or other editorially independent information published on this site. This protocol controls the exchange of data between devices. The Sixth Edition will remain available through select Library Subscription Services where prior licensing agreements are in place. IP addresses are comparable to your mailing address, providing unique location information so that information can be delivered correctly. East,Adelphi, MD 20783. LANs connect computers and peripheral devices in a limited physical area, such as a business office, laboratory, or college campus, by means of links wires, Ethernet cables, fibre optics, Wi Fi that transmit data rapidly.

News and success stories
Following are the nonproprietary Internet applications and the protocols at application layer used by them. 6 Wireless Local Area Networks WLAN. Transmission media is broadly classified into two groups. That is the type of service we offer. Networking is perhaps the most important and useful area of computing to learn when looking for an IT career. After more than 20 years on the Internet, AcademicInfo has become the premier website for education and university related information and reviews. Many in this field also pursue a bachelor’s degree and certifications to deepen their knowledge and value. Although this is a beginner course, it may be too difficult for some. This course is also part of the Google IT Support Professional Certificate, one of the most popular Google Certification on Coursera. Computer Networking Appendices ATopDown Approach 7th ed. These include four key components. Regardless of your system’s purpose, it will need a connection protocol to link all devices. Free top tips for speeding up a slow Windows laptop or desktop computer in 2022. Some familiar examples of application layer protocols, built on these lower protocols, are HTTP for accessing web content, SSH, and TLS/SSL. What is a cyclical redundancy check. What is TCP/IP in computer networking. There are a variety of protocols available to build networks. He is also the Next G Wireless Faculty Lead at Virginia Tech’s Innovation Campus. Monday to ThursdayPhones: 8:30 a. The positions offer attractive remuneration and plenty of space for growth and development as per your skills, experience and expertise in the field. The History of Networking since the early times of computers. An engineering degree will teach you the foundation of networking regardless of vendor. Networks follow protocols to make communication possible between connecting devices. Such service is provided by Skype, Google Talk, Windows Live Messenger, Yahoo Messenger, etc. Never Die Network Based on Cognitive Wireless Network and Satellite System for Large Scale Disaster. Undergraduate Tuition: $6,565. Internet connections are an essential part of the world, as we all use the web to search for information. Try out the Workshops section of this website here: Workshops Login required. Upon completion of this certificate, you’re encouraged to take the Cisco Networking Academy certification exam at your local CCNA testing center.

How SASE Helps Overcome Remote Access Challenges
An example of WAN is the Internet, which connects billions of computers globally. Students who plan to seek employment at the bachelor level are advised to take one of the concentration area curricula in addition to the general and departmental requirements. Students will learn to design and configure LANs and WANs, install network hardware and software, understand and configure network topologies, construct and install cabling solutions, manage user accounts, monitor and analyze network performance, and perform basic troubleshooting. Hotspots can be set up at home, office or any public space. Standards are a set of data communication rules required for the exchange of information between devices and are developed by various standards organizations, including IEEE, the International Organization for Standardization and the American National Standards Institute. Collaboration tools are key as businesses shift to hybrid work. This includes study at a public TAFE or other VET provider, whether a qualification was completed or not. Join now to share and explore tons of collections of awesome wallpapers. CTU is accredited by the Higher Learning Commission. The cost of a computer networking degree varies, depending on the degree level and whether you study on campus or online or attend a public or private school. Billions of devices connect to the network every day. 21 Best Technical Analysis Software for Stock Trading in India 2023. To do this, you will need to be knowledgeable of the terms and technologies involved in networking. By using this website, you agree with our Cookies Policy. List the seven layers of the OSI model and the four layers of the TCP model. This course is the first of a series that aims to prepare you for a role as an entry level IT Support Specialist. In addition to this, it’s also important to be able to work well under pressure and have excellent communication skills. Learn about Online College Admissions at WGU. Services pay per use model5. This conceptual framework outlines the functions of a networking system. Back to the computer dictionary. However, there are some significant job perks for those who qualify for these positions. For example, network professionals that know how to implement and manage cloud resources using public cloud providers like AWS, Azure, or Google Cloud can have the upper hand. Students who do not have an undergraduate degree in Computer Science, Computer Engineering, Electrical Engineering, or Telecommunications Engineering are required to take the following courses before they apply. At large companies, they work on teams that can include IT help desk employees, admins, network operations staff, and developers. Most of the applications you use are on the Application Layer, with the complexity of the other layers hidden. One of their most important responsibilities is getting a network back online and working properly after there’s been an outage. Typically, routers are placed on the backhaul network, and they in turn may have their own backhaul networks that serve many edge devices.
Share this:
Bureau of Labor StatisticsNote: Many employers don’t specify any years of experience in job postings. Other roles that could draw on your knowledge include systems analyst and network hardware engineer. There are deep packet inspection tools and flow based tools. ACADEMICCOURSES connects students with educators providing courses, preparatory years, short programs, certificates, diplomas, and more. Major products of networking equipment manufacturers include switches, routers, and network control equipment. Explain the function of hubs, switches, and routers. This program is designed to help prepare you for work in network administration for corporate, government, or nonprofit organizations. People don’t often understand the distinction of what happens locally versus what happens remotely. In Bit Torrent, suppose Alice provides chunks to Bob throughout a 30 second interval. A network link connects nodes and may be either cabled or wireless links. We’ll learn about the IP addressing scheme and how subnetting works. But remember, specialization is what will set you apart from the rest.
Cisco Certified Internetwork Expert Enterprise Infrastructure
To view program requirements, including required courses, electives, course descriptions, and credit hours, visit. BackboneBandwidthBasebandBase stationBDCBeowulfBERBERTBGMPBGPBindBisyncBitnetBit stuffingBittorrentBlackBerry Enterprise ServerBlackBerry MessengerBladeBlade serverBNCBNC ConnectorBOINCBOOTPBootstrap protocolBorder Gateway ProtocolBottleneckBPDUBPLBPSKBranchCacheBridgeBroadbandBroadcastBroadcast addressBroadcast domainBrouterBSDIBSSBSSIDBurstBus topology. Additional resources for Computer Networking A top down approach 7th ed. Get help and share knowledge in our Questions and Answers section, find tutorials and tools that will help you grow as a developer and scale your project or business, and subscribe to topics of interest. THE CERTIFICATION NAMES ARE THE TRADEMARKS OF THEIR RESPECTIVE OWNERS. Adding CompTIA Linux+ and Server+ will also help you begin your career in this field. The resulting measurements are then expressed as a per second number. TAKE OUR CAREER TRAINING READINESS KIT. Tablet based kiosks became increasingly popular for customer self service during the pandemic. It is often the case that network engineers work directly with clients on top of maintaining their usual duties. For example, when you perform backups, you often put great strain on the bandwidth and can thus easily recognize shortages or bottlenecks. Learners will gain skills in designing cloud infrastructure and services and in recommending cloud security solutions, policies, and procedures. Stanford School of Engineering.
MSc in Computer Networking
This hardware could be electronic devices like fax machines, computers, printers, and other IT infrastructure. Here are a few networking trends that you can join if you start in the field now. Introduction to Spreadsheets helps learners become proficient in using spreadsheets to analyze business problems. Applications are accepted on a rolling basis throughout the year. In this paper, we consider a multi antenna dual functional radar communication DFRC satellite system, where the satellite has a dual capability to simultaneously communicate with downlink satellite users SUs and probe detection signals to a moving. This makes network architects some of the highest paying jobs in the field. Local Area Network LAN: A computer network that is connected within a physical space. A node is essentially any network device that can recognize, process, and transmit information to any other network node. I was with Amazon at that time. Our Computer Networking degree helps you get hands on, real world job experience here on campus and beyond through. All the online engineering, Computer Science, and Electrical and Computer Engineering courses are administered by the Engineering Online unit within the College of Engineering. GUI Graphical User Interface – A computing user interface UI characterized by a full screen work area and icons that represent objects such as folders and files. Not only will students gain a full understanding of how computer networks are designed and deployed, they will have the opportunity to gain hands on experience by applying their lessons in real world applications. General strategies available for achieving remote visualization fall into four rough categories. Softcover ISBN: 978 3 319 85063 4Published: 04 May 2018. Students can buy a shareable certificate of completion, but they don’t have to pay to take the class. Overall a great introductory course to learn about Computer Networking basics and essential Computer network protocols. WGU is fully accredited by the Northwest Commission on Colleges and Universities to confer this computer networking degree to aspiring networking professionals. Companies show an increased interest in computer networking experts who know how to work with OpenFlow switches and controllers or Data Center solutions such as VMware NSX or < Cisco's Virtualized Multiservice Data Center. Marking the longest single sortie for the twin fuselage, 385 ft.
Some extra tips to keep in mind
If you have not started yet, please enroll in your most favorite course, start it and finish it. SolarWinds Hybrid Cloud Observability. Participate in the design and execution of vulnerability assessments and security audits. Expand Your Career Expand Your Network and Develop Leadership Skills as an ISACA Member. Featured or trusted partner programs and all school search, finder, or match results are for schools that compensate us. MindTap Networking provides additional hands on practice and certification test prep. Each port is numbered for ease of indentification. Bandwidth calculation will depend on the organisation and what users do within the company. Buy a computer, take it apart and put it back together again. They can help you improve and develop your academic skills and support you in any area of your study in one on one and group sessions. In a network, multiple nodes are used. But please note, after the evaluation of the content, select concepts from the Sixth Edition are still viable project management practices. You can check out user reviews or speak to a professional who can help you select a suitable router. A network certification may set you up with the skills and knowledge needed to progress in an IT network career. The sigNow extension was developed to help busy people like you to reduce the stress of signing documents. Herzing University offers an accelerated online degree program in computer networking. The more sophisticated the transmitting and receivingtechnology, the narrower each bit can become and, thus, the higher thebandwidth. It allows you to radically reduce dwell time and human powered tasks. You’ve reached your limit of 10 Favourites.
Free Courses in Hindi
They install internet connections and electronic cabling. Fort Hays State University in Hays, Kansas offers an online Bachelor of Science in Information Networking and Telecommunications, with a concentration on Computer Networking and Telecommunications degree program, ideal for students who wish to pursue careers in computer and network organizations and telecommunications companies. Frequency hopping is anadditional measure that also enables data security. The term bandwidth is normally used in internet broadband subscription plan. Login details for this Free course will be emailed to you. So the need for network technology will always exist, more or less. Get a personalized tour of our campus and your program. How do some of the industry’s leading players define these essential and closely related security terms. Curriculum: Introductory. Although the encryption and decryption can be done by other layers of the application or the session layer, each has its own set of disadvantages, and that is why this layer takes care of that. Every day spent working in computer networking will feel like a day well spent. Many smartphones offer hotspots too. You can use an entry level IT credential like the CompTIA A+ to prepare. This specialization consists of four courses that are very helpful for those who wish to develop computer network security skills. Wallpaper computer networking background wallpapers images. Topic5 Example of preference revelation 2021. Cisco company has six levels of Network Certifications; entry, associate, specialist, professional, expert and architect. ZDNET Recommends’: What exactly does it mean. Methods of network message encoding vary depending on the transmission medium. You need to configure a SOHO Small Office Home Office network to be easily discovered by guest users.
Chapter 4: Network Layer: Data Plane
Scheduled live, interactive online sessions led by an experienced practitioner. Typically, a network engineer has more education and earns more than a network administrator. More Podcasts The Telnet Protocol in Anchor Podcast The HTTPS in iHeart Podcast The FTP Protocol iHeart Podcast The OSI Model in Google Podcast The DNS Protcol in Google Podcast. ” Recognized as a leading cybersecurity provider, getting certified on Palo Alto Networks is a valuable credential for those seeking advancement in network security. Network engineering is experiencing incredible growth, and there are ample opportunities for women who want to enter this exciting and in demand field. Areas of specialization may range from routing and switching, security, wireless, service providers, Unified Communications Voice and Video networks, mobile networks, or data centers. Looking for reliable computer support near you. In addition to these topics, this book also emphasizes paired and fixed coverage of ADSL, 3G cellular, gigabit Ethernet, MLPS, and peer to peer networks. The full time standard undergraduate tuition fee for the Academic Year 2022/23 is £9,250 per year. Some of the majorly required skills are – an understanding of UNIX/Linux based environments, knowledge of automation software and cloud computing services, scripting skills, etc. Bureau of Labor Statistics BLS predicted in a 2016 study that network engineer employment would grow by 6% over the following ten years, and studies suggest that the number of network jobs in the field currently exceeds the number of qualified candidates, presenting an excellent opportunity for interested and qualified applicants. The world is full of such type of programs: for example, the web browser you are using to read this website is a piece of software that connects to a remote computer where the data is stored and grabs the text content to display on your screen. Although it will not carry credit, you can be assured of a rich learning experience as you navigate through the sessions. This course is made up of interactive quizzes, industry professional led seminars, and other multimedia learning content. This course heavily focuses on the fundamentals of computer networking.
“Welcome to the eighth edition of Computer Networking: A Top Down Approach Since the publication of the first edit
✅ WiFi and cellular communication. It especially focuses on your expertise in advanced automation, scripting, network security, and architecting knowledge all within the AWS framework. Com are the property of their respective owners. Upon completion, students are eligible to purchase a certification in the Alison shop if they would like to. Knowing specific technologies and security protocols is important, but having base level knowledge is crucial. At WGU, we design our curriculum to be timely, relevant, and practical—all to help you demonstrate what you know. Most computer networks include all the following components. We have streamlined the network engineering and security courses so that you can benefit from your prior coursework and your professional experience. Upon successfully completion of this module student should be able to sit for CCNP Route industry certification subject to satisfying relevant pre requisite CCNA. It takes around six to ten hours and a final assessment is administered upon completion. I share Java tips on and. TCP/IP is the globally accepted set of protocols that allow computers and other devices to send and receive data through the Internet. And not be tied directly to job tasks. Those who achieve CCNP have demonstrated the skills required in enterprise roles such as network technician, support engineer, systems engineer or network engineer. 1 specification RFC 2616. G, twisted pair, coaxial cable and optical fiber. SaaSSambaSANSAPSATANSatelliteS bandS band Multiple AccessSDLCSDSLSDUSecond level domainSegmentSequenced Packet eXchangeSerialServerServer farmServer mirroringService Advertising ProtocolSession layerSFTPShareShared directoryShared folderShielded Twisted Pair cableShort haulSign offSign onSingle mode fiberSitenameSLASLDSLIPSMASmart homeSmart terminalSMBSMSSMTPSmurf attackSNASneakernetSniffingSNMPSOASOCKSSONETSpanning treeSpanning tree protocolSPDYSPISpoofSpoofingSpread spectrumSPXSSAPSSHSSHDSSIDSSLSSTPStackStadiaStar topologyStateful firewallStatelessStaticStatic allocationSTMSTM 1STM 4STM 8STM 16STM 64Store and forwardSTPSTP CableStraight throughStreaming contentSTSSTS 1STS 3STS 12STS 24STS 48STS 192SubdomainSubnetSubnet maskSubnetworkSupercomputerSwitchSymmetricalSYNSYN attackSyncthingSyslogSYSOPSystem administratorSystem operator. Potential career positions after graduation include Computer Network Architect, Network Administrator and Computer Support Specialist. Depending on the device, it is possible to increase both rates. Although it is a beginner level course, it has been taken by many students who want to learn networks and are also considering their options with computer networks. Bare RTP, the service quality suffers if the network is unreliable. Additionally, WANs transmit data at slower rates than LANs do. Introduction to Networking. I was wondering if there is was a typical way of comparing the ROC curve where essentially I will be using the same model but on two different data sets to show they are similar. It is the official Instagram account of Avrupa Networking. An Associate Degree in Network Administration can take about two years to complete.
Cyber Security
Recent developments in the networking industry have increased the demand for networking professionals in India. This is one of the best network engineer online training courses offered by LinkedIn and is specially designed to prepare you to apply for a junior network engineer role. There are also videos on how to set up your own router and switch. Quality of Instruction: Excellent. Some colleges will even let you start earning graduate credit during your bachelor’s degree program. Programmers use various programming languages, code libraries, and protocols to do the work. What is Autonomous system – Full Explained. There are many benefits to participating in this program. BIOS Basic Input/Output System – The system firmware in older computer systems and some modern systems responsible for orchestrating hardware registration during bootup, locating and passing control to a bootable operating system, and then carrying out various instructions, from the operating system and its drivers, directed toward system hardware and its input/output I/O interfaces. Adjusting the amount of rendering performed on a local server versus on a remote client in order to optimally utilize resources, such as available bandwidth between the server and the client. What is SSH Secure Shell, and What are its Features. PC Mag, Dynamic IP Address. Hence, one has to gain deeper visibility into the performance of hardware devices to address the minutest problems. Administrators typically handle more network related responsibilities than support specialists. Class ANetworkE mailRing topologyMesh topologyNetwork serverUsernameCommunication deviceDownloadHub. Some of the most commonly used terms in day to day networking life are as discussed below. Some modern modems have routers built in. Completing a computer networking program can be a valuable asset for your resume as you apply for jobs in this in demand field. What is Backbone Network Backbone Network Deep Learning. CTOs often work alongside CIOs. More from Rowell: Twitter: Website: Clear to Send: Twitter: YouTube: learToSend Website: Check out our Patreon – ollow us on Twitter Follow us on Instagram Like us on Facebook oin the group on LinkedIn heck out our website MerchContinue reading “Ep 111 – Wireless Networks”. Table of ContentsExamples of the Computer NetworkTypes Of Computer NetworkLocal area NetworkMetropolitan Area NetworkWide Area NetworkMain components of the Computer NetworkNodesEnd NodesMediaWired MediaWireless MediaSome of the examples for both wired MediumSome of the exampled for the wireless mediumFault ToleranceScalabilityQuality of ServiceAdvantages of the Computer NetworkDisadvantages of the Computer NetworkSecurity in the Computer NetworkSummarySecond Explanation of Computer NetworkCommunication systemCommunication ProtocolsBenefits of Computer NetworkWhat Elements Makes Networking Possible. By signing up/logging in, you agree to our Terms and condition • Privacy Policy.
Contributor Guidelines
Web development, programming languages, Software testing and others. You can also use the Sumita Arora python class 12 book to prepare for competitive exams like Olympiad, GATE, and IIT JEE. Use Git or checkout with SVN using the web URL. Each branch is significantly different and each has their own training and benefits. LAN local area network. Bandwidth is not a measure of network speed – a common misunderstanding. This online course is an awesome resource to start with computer networking. Fill out the form below and we’ll get back to you as soon as possible. 50 Attempts5 Q : 15 mins. Fill up your details to notify you when this book will be available. What is the refund policy. There are many tools, applications and utilities available that can help you to secure your networks from attack and unnecessary downtime. Major coursework provides the impartation of skills needed for the identification, analysis, and integration of information technologies and application of existing standards to primary concerns in information technology. Options are available based on role or technical area and by level:FoundationalAssociateProfessionalSpecialty. NB IoT is a communication standard designed for IoT devices to operate via carrier networks, either within an existing GSM bandwidth used by some cellular services, in an unused “guard band” between LTE channels, or independently. Specializing in e learning and e courses. The asymptotic bandwidth formally asymptotic throughput for a network is the measure of maximum throughput for a greedy source, for example when the message size the number of packets per second from a source approaches close to the maximum amount. The most common kind of networking hardware today is a copper based Ethernet adapter which is a standard inclusion on most modern computer systems. A socket is an object that you create, configure and on which invoke some functions to send or receive data. This also means that technology will continue to change, so you will have to learn to keep up with the changes. Routers examine incoming packets to determine the appropriate destination IP address and then forward the packet to that destination. Our learning model is just one of those. Sign in or create an account to save jobs. In the age of sustainability in the data center, don’t.
Your Choice Regarding Cookies On This Site
Curriculum: Intermediate. Please contact us if you would like a free therapy session. Knowing specific technologies and security protocols is important, but having base level knowledge is crucial. The most common topologies are described below. Planning your finances before you come to university can help to reduce financial concerns. Chapter 1 Computer Networks and the Internet. Which is a feature of Internet Protocol version 6 IPv6. The internet, online search, email, audio and video sharing, online commerce, live streaming, and social networks all exist because of computer networks. These can be quite difficult to pass. So check it out and subscribe today. 3 of packet switching versus circuit switching in which an example is provided with a 1 Mbps link. Scan this code with your phone’s camera. Discrete Math: Functions and Relations is designed to help students develop competence in the use of abstract discrete structures fundamental to systems networking. The amount you earn depends on factors like industry, company, location, and experience. Acceptwhile 1:sentence = connectionSocket. How to Become a Cybersecurity Engineer.